What is a Honeypot?
The ever-expanding world of technology is growing bigger every day. With that comes a myriad of vulnerable and insecure computer systems that have been neglected. This presents a massive problem, as these uncared-for systems are goldmines for cybercriminals to access.
With this malicious access comes data leaks, stolen credentials, and a plethora of other exploits that could harm an organization. To combat this, Careful Security implemented a honeypot, a trap, to lure attackers and expose their methods in the process. We then learn from these attackers’ methods and use that knowledge to better secure organizations’ internal infrastructure.
Why do you need a Honeypot?
A honeypot is a decoy system implemented in an organization’s network with the purpose to detect, deflect, and study hackers’ attack methods. Placing a honeypot in a network, or cloud environment, can lessen the risk of a real target being infiltrated by posing as a vulnerable system within an organization. The honeypot lures attackers in and exposes them, which allows Careful Security to track and monitor their every step. Having a honeypot in a network can be a powerful defense-in-depth tactic to further protect an organization’s data against cybercriminals.
What We're Seeing Right Now in the Cyber Landscape:

The example above is from a fresh honeypot that Careful Security implemented less than 24 hours ago. As you can see, there have been almost 60,000 attacks in this short time, proving why security is so vital to a company.

Here we have an example of the top 10 Common Vulnerabilities and Exposures (CVE) used in an attempt to access our honeypot. Careful Security uses this information to study and further protect systems from vulnerabilities.
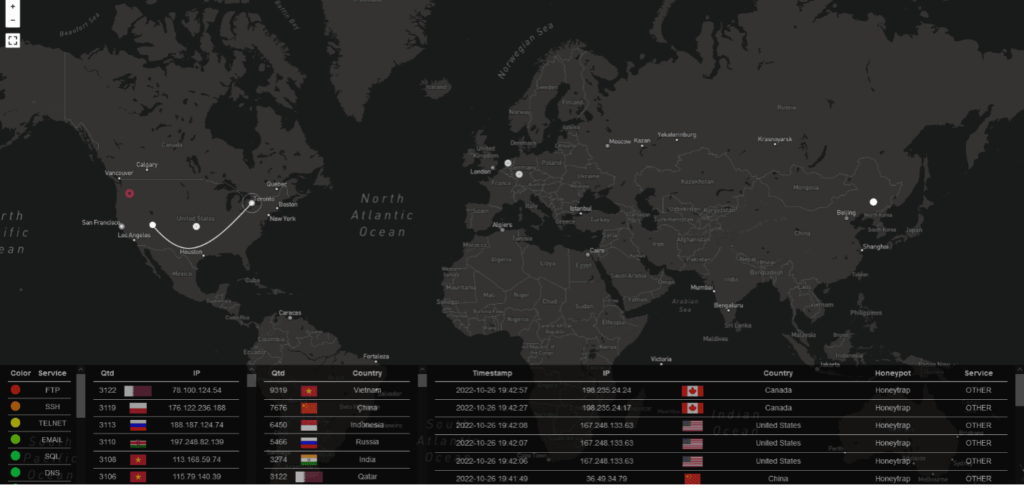
Another feature of the Careful Security honeypot is a live, interactive map where we are able to monitor where and when an attack is, and which service or port hackers are attacking.
Careful Security has access to a wide variety of capabilities with this state-of-the-art honeypot, all of which better protect an organization’s data from attackers. From exposing which vulnerabilities are frequently being exploited to understanding the current cyber threat landscape with our live interactive attack map, the honeypot is an immensely valuable tool in Careful Security’s arsenal.

