Protect Your Information Assets
Detect Cyber Attacks
Gain visibility to prevent attacks

Data Security
Manage the risk associated with Personal Identifiable Information (PII) and other sensitive data.
Learn moreSee Everything, Stop Anything: Early Threat Detection With SIEM
Threat Detection & Security Visibility

Exposure
Traditional log management scatters data, making it hard to spot threats. Malicious activity hides, potentially leading to breaches. Delays in identifying suspicious events increase security risks.
Benefits
- Early threat detection: Identify suspicious activity quickly and minimize potential damage.
- Faster response times: React to incidents swiftly and effectively.
- Improved security posture: Gain valuable insights to strengthen your overall security.
Methodology
Our phased approach simplifies SIEM implementation:
- Data Collection: Streamline log gathering from all critical systems.
- Log Analysis: Format your data for efficient threat detection and investigation.
- Alert Configuration: Customize alerts to prioritize high-risk events.
- Ongoing Support: We continuously monitor and ensure optimal SIEM performance.
Sample Report
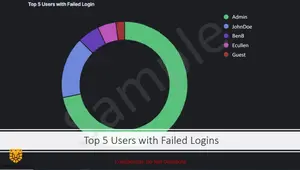
Expose Hidden Risks: Identify External Vulnerabilities With
Attack Surface Monitoring

Exposure
Traditional security often misses shadow IT and outdated systems. These hidden attack vectors leave you vulnerable to breaches.
Benefits
- Uncover hidden assets: Identify and address unknown devices before they become entry points for attacks.
- Real-time threat detection: Receive immediate alerts on newly discovered vulnerabilities.
- Proactive risk management: Minimize the risk of breaches with continuous monitoring.
Methodology
- Discover Assets: We identify all connected devices and systems.
- Set Up Alerts: Tailor alerts to prioritize high-risk vulnerabilities.
- Continuous Monitoring: We continuously monitor your attack surface for threats.
- Remediation: Address identified vulnerabilities to prevent future occurrences.
Sample Report
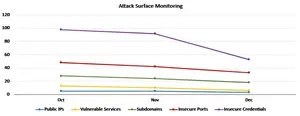
Stop Phishing Scams In Their Tracks
Advanced Email Security

Exposure
Traditional email leaves you vulnerable to phishing attacks and data breaches. Sensitive information can be:
- Accidentally leaked: Employees might unknowingly send confidential data.
- Intercepted by attackers: Hackers exploit vulnerabilities for unauthorized access.
- Non-compliant with regulations: Failure to meet data security standards can result in penalties.
Benefits
- Advanced Phishing Protection: Block malicious emails and attachments before they reach your inbox.
- Data Loss Prevention: Prevent accidental or intentional data leaks.
- Enhanced Security: Encrypt sensitive information for secure communication.
- Compliance Assurance: Meet regulatory requirements and demonstrate data security commitment.
Methodology
Our experts analyze your email security posture, focusing on:
- Authentication Protocols (DMARC, DKIM, SPF): Verify email sender legitimacy and prevent spoofing.
- Phishing Detection: Identify and remove phishing attempts before they compromise your data.
- Malware Protection: Block malicious attachments and downloads.
Sample Report

Safeguard Your Data
Comprehensive Data Security Monitoring

Exposure
Data breaches erode trust & cripple business. A single incident can cause:
- Customer Loss: Leaks damage trust, leading to customer churn.
- Financial Impact: Fines, lawsuits, and remediation costs drain resources.
- Reputational Damage: Negative publicity harms your brand image.
Benefits
- Enhanced Security: Proactive monitoring shields data from threats.
- Compliance Assurance: Meet industry regulations and avoid penalties.
- Customer Trust: Demonstrate commitment to data protection.
Methodology
We go beyond reactive measures. We find the root cause of potential vulnerabilities to prevent breaches before they happen
Sample Report
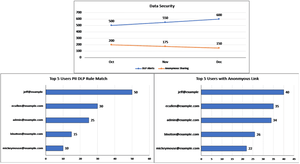
Stop Advanced Threats: Endpoint Detection & Response
Device Security

Exposure
Traditional security misses hidden threats. Unpatched devices & open ports create vulnerabilities.
Benefits
- Advanced Threat Detection: Block viruses, malware, and ransomware attacks.
- Patch Management: Prioritize and deploy critical security updates.
- Endpoint Visibility: Gain real-time insights into device security posture.
Methodology
We harden endpoints, apply security policies, and use advanced tools to detect and respond to threats.
Sample Report
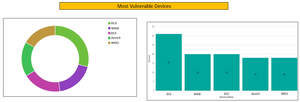
Patch Your Weaknesses:
Proactive Vulnerability Management

Exposure
Blind spots leave you vulnerable. Unpatched systems & unseen threats create risks.
Benefits
- Identify & Patch Vulnerabilities: Close security gaps before attackers exploit them.
- Advanced Threat Detection: Uncover hidden threats hiding on your endpoints.
- Actionable Insights: Gain visibility to prioritize remediation efforts.
Methodology
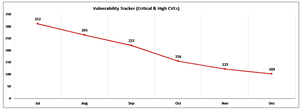
We scan systems, prioritize risks, and provide reports to guide vulnerability remediation.
Sample Report
Tailored reports that provide actionable insights, highlight critical vulnerabilities, and track remediation progress.
FAQ
What Is Your Contract Duration?
We have 3-month contracts and if you’re not satisfied with the service you can cancel anytime with a month’s notice.
Spoiler Alert: Everyone loves our monitoring services.
How Should I Schedule A Demo?
Email us for a demo and we’ll walk you through the process and give you access to a trial version.
What Tools Do I Need?
You don’t need to buy any tools to get the monitoring started. We’ll ingest your logs and start providing valuable insights within a week of onboarding.
Can You Conduct Breach Investigations?
Yes, we can review your application and infrastructure logs and uncover security events.
