The Price of a Pentest: Why Your Annual Penetration Test Isn't Protecting Your Next Enterprise Deal
"The definition of insanity is doing the same thing over and over again and expecting different results."
—Often attributed to Albert Einstein
You're a SaaS company with 300 employees. You've built something special—a product that Fortune 500 companies actually want. But every enterprise deal hits the same wall: the security questionnaire. "Please provide your most recent penetration test report." You hand over the PDF from six months ago. The procurement team reviews it, frowns, and asks follow-up questions your report doesn't answer. The deal stalls. Sound familiar?
Or maybe you're a healthcare organization with 500 employees. You passed your HIPAA audit. You run an annual pentest. And yet every time you read about another breach—Yale New Haven Health's 5.6 million patient records, United Healthcare's $2.87 billion disaster—you wonder: would we catch it in time?
I've been on both sides of this equation—as the person ordering pentests for Fortune 500 companies and as the one delivering them to growing mid-market businesses. And I can tell you that the way most organizations approach penetration testing is fundamentally broken.
Not because the testers lack skill. Not because the methodologies are flawed. But because we've turned a powerful security tool into an expensive compliance ritual that satisfies auditors while leaving the actual attack paths wide open.
The 2026 Reality Check
Let's look at what's actually happening out there.
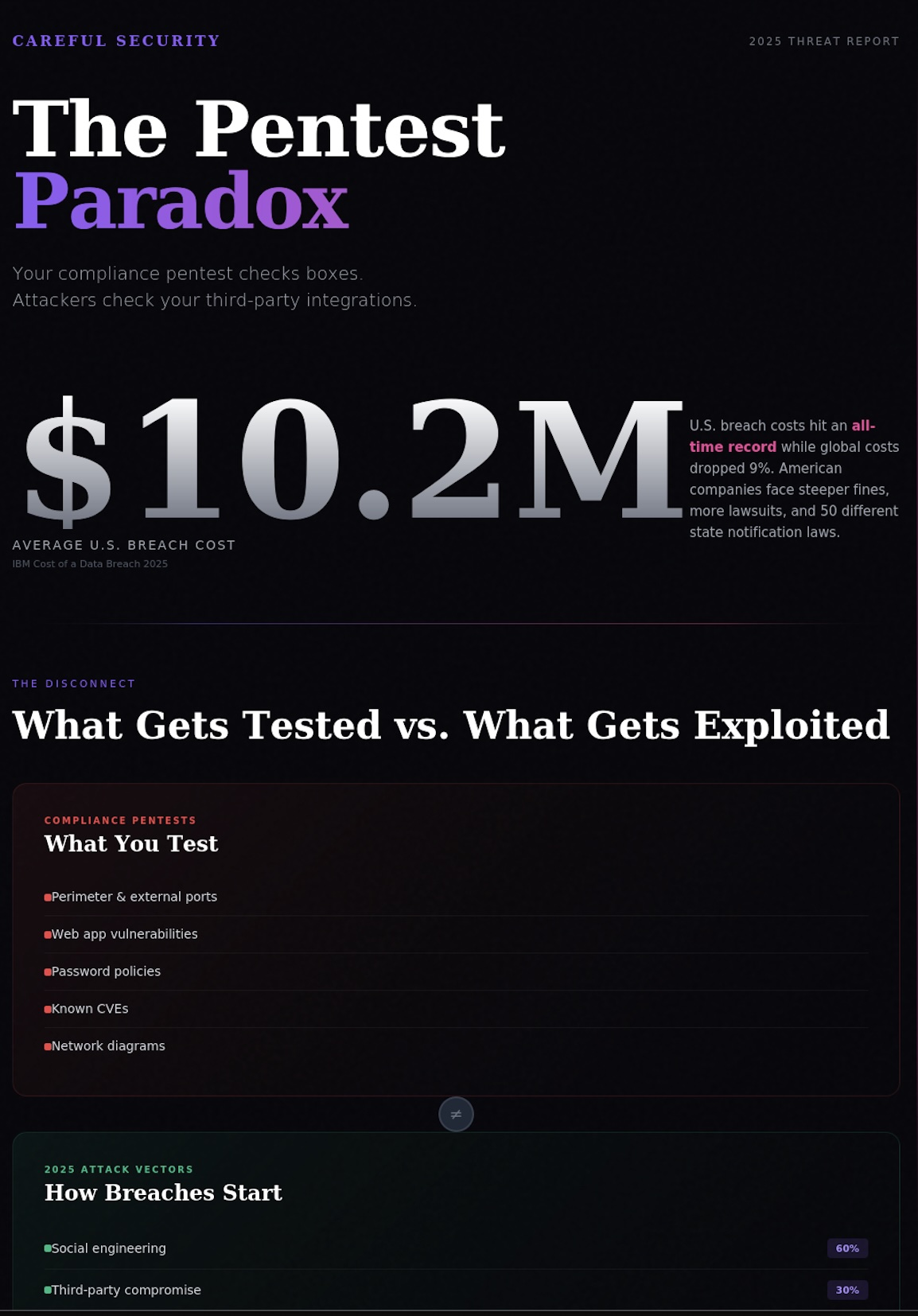
According to IBM's 2025 Cost of a Data Breach Report, U.S. breach costs just hit a record $10.22 million—while the global average dropped to $4.44 million. Why the divergence? American companies face steeper regulatory fines, more class-action lawsuits, and the complexity of 50 different state notification laws. If you're a mid-market company operating in the U.S., you're playing in the most expensive breach environment on the planet.
The Verizon 2025 Data Breach Investigations Report analyzed over 22,000 security incidents. The findings should keep every CEO up at night: ransomware is now present in 44% of all breaches—up 37% from last year. Third-party involvement in breaches doubled to 30%. And here's the gut punch for smaller companies: 88% of breaches involving SMBs contained a ransomware component.
The attackers aren't targeting you because you're important. They're targeting you because you're accessible. And that annual pentest sitting in your SharePoint folder? It's not telling you what they already know.
The Compliance Trap
SOC 2, ISO 27001, HIPAA, PCI DSS—they all require or strongly recommend penetration testing. So companies check the box. They hire a vendor, schedule a test for the same week every year, receive a 200-page PDF, and move on with their lives.
The problem? Compliance-driven pentests are designed to satisfy auditors, not attackers.
Consider what the Verizon DBIR tells us about how breaches actually start: credential abuse (22%), phishing (16%), and vulnerability exploitation (20%—up 34% from last year). The exploitation spike? Edge devices and VPNs now account for 22% of vulnerability-based breaches, an almost eight-fold increase from just 3% in 2024.
Yet most compliance pentests focus on your web application and perimeter scanning. They're checking if your front door is locked while attackers are coming through your Palo Alto firewall's zero-day vulnerability or your Salesforce integration's misconfigured API.
A View from the Trenches
We conducted a penetration test for a healthcare organization last year. About 400 employees, multiple clinic locations, electronic health records—the works. They had passed three consecutive HIPAA audits. Their previous pentest reports showed minimal findings. On paper, they were secure.
Within four hours, we had domain admin access.
How? We didn't use a zero-day exploit or some sophisticated nation-state technique. We called their help desk, pretended to be a new IT contractor who had been locked out, and convinced them to reset credentials for an account we had identified through LinkedIn research. Classic vishing—the same technique that brought down M&S in April 2025. That attack cost the British retail giant £40 million per week in lost sales.
Their previous pentests had never included social engineering. Why? Because their compliance framework didn't require it, and testing humans is messier than testing machines. The auditor was happy. The checkbox was checked. But the organization was wide open.
Here's what makes this personal for healthcare: IBM found that healthcare breaches take an average of 279 days to identify and contain—five weeks longer than any other industry. At $7.42 million per incident, that's the most expensive breach cost of any sector. Every day you don't know about an attacker in your network is a day patient records are being exfiltrated.
Organizational Realities
The Third-Party Blindspot
In August 2025, Salesloft's Drift chatbot was compromised, leading to unauthorized access to the Salesforce environments of over 700 organizations. Google, Allianz Life, Air France-KLM—all breached through a third-party integration they probably never thought to test.
If you're a B2B SaaS company, your customers' security questionnaires are about to get a lot harder. They're going to ask about your third-party integrations, your API security, your vendor risk management. And "we run an annual pentest" isn't going to cut it anymore.
Third-party breaches doubled in 2025, now accounting for 30% of all incidents. Supply chain compromise is the second most common attack vector after phishing—and the second most expensive at $4.91 million per breach. Yet most pentests explicitly exclude third-party integrations from scope because "that's not our system."
The Shadow AI Problem
Here's a new wrinkle your last pentest definitely didn't cover: shadow AI.
IBM found that 20% of breaches in 2025 involved unauthorized AI tools—employees using ChatGPT, Claude, or other services without IT approval. These shadow AI incidents added $670,000 to the average breach cost. And 97% of organizations that experienced an AI-related security incident lacked proper AI access controls.
Think about it: your employees are copying sensitive customer data, source code, and financial projections into AI tools every day. Are your pentests looking at that? Are your compliance frameworks even asking the question?
This is why ISO 42001—the new AI governance standard—is becoming table stakes for enterprise procurement. Companies that get ahead of this will have a competitive advantage. Companies that don't will find themselves explaining to prospects why their employees were pasting customer data into public AI models.
The SMB Target
If you're a mid-market company—200 to 2,000 employees—the data should make you uncomfortable. Verizon found that 88% of breaches involving SMBs contained a ransomware component, compared to only 39% for enterprises.
Why the disparity? Large enterprises have dedicated security teams, 24/7 SOCs, and the budget to deploy advanced detection tools. Mid-market companies often have one overworked IT director trying to manage security alongside everything else. Attackers know this. Ransomware gangs specifically target the middle—companies big enough to have valuable data and pay ransoms, but small enough to lack mature defenses.
The median ransom payment in 2025 was $115,000. But that's just the ransom. Add business interruption, incident response, legal fees, notification costs, and regulatory fines, and you're looking at millions. For a 500-person company, that can be existential.
What Business Value Actually Looks Like
A penetration test should answer business questions, not just technical ones. Before your next engagement, step back and ask:
For B2B SaaS: What would make us fail our next enterprise security review? Your prospects are going to ask about your pentest scope, your remediation timelines, and your third-party risk management. Can your current pentest report answer those questions—or does it create more concerns than it resolves?
For Healthcare: Could an attacker reach patient records from a compromised workstation? HIPAA requires you to protect PHI, but your pentest might stop at the perimeter. What happens when—not if—someone clicks a phishing link? Can your current controls detect lateral movement before 279 days pass?
For Manufacturing: Are your OT systems segmented from IT? Espionage-motivated breaches in manufacturing jumped 163% in 2025. Nation-state actors are after your designs, your processes, your supplier relationships. Intellectual property theft costs $178 per record—the highest of any data type. Is your pentest even looking at your production floor?
For Everyone: What would our board need to know tomorrow if we were breached today? A good pentest doesn't just find vulnerabilities—it tells you which ones would actually hurt your business and how quickly you could detect and respond to a real attack.
Root Causes: What 2025 Breaches Tell Us
Let's map recent high-profile breaches against what typical compliance pentests would have caught:
M&S (April 2025): Social engineering attack via help desk impersonation, leading to Active Directory compromise and DragonForce ransomware deployment. Losses estimated at £40 million per week. Root cause: Human factor untested.
Salesloft/Drift (August 2025): Third-party chatbot compromised, exposing Salesforce environments of 700+ organizations including Google and Allianz. Root cause: Third-party integrations out of scope.
Qantas (June 2025): Attacker targeted call center, gained access to third-party customer servicing platform, exfiltrated 5.7 million customer records. Root cause: Social engineering + third-party platform = invisible to standard pentest.
European Airports (September 2025): Ransomware attack on Collins Aerospace's vMUSE system disrupted check-in at Heathrow, Brussels, and Berlin airports. Root cause: Supply chain attack on shared vendor platform.
Jaguar Land Rover (September 2025): Ransomware disrupted manufacturing across multiple UK plants. Estimated cost: £1.9 billion—the most economically damaging cyber event in UK history. Root cause: IT/OT convergence created unexpected attack paths.
Notice the pattern? Social engineering, third-party platforms, supply chain vulnerabilities, and IT/OT boundaries. These are the actual attack vectors causing billions in damages—and they're systematically excluded from most compliance-driven pentests.
Tools, Resources & Solutions
Here's how to transform your next penetration test from a compliance checkbox into a competitive advantage:
Scope for Your Actual Risk, Not Your Compliance Requirement
Before defining scope, gather intelligence on how organizations in your industry are actually being attacked. The MITRE ATT&CK Framework maps adversary tactics and techniques by industry. The Verizon DBIR breaks down attack patterns by sector. Use this data to drive your pentest scope.
If ransomware groups are targeting VPNs and edge devices in your sector—and they are—that's where testing should focus. If supply chain attacks are the second most common vector, your third-party integrations need to be in scope. Stop testing what's convenient. Start testing what's dangerous.
Include Your People
Sixty percent of breaches still involve the human element. Every major breach of 2025—M&S, Qantas, MGM—started with social engineering. If your pentest doesn't include phishing, vishing, or pretexting, you're testing with one eye closed.
But don't stop at click rates. Test your detection and response. Did anyone report the suspicious call? Did your security team notice the anomalous login? How quickly was the compromised account locked? These metrics matter more than whether Susan in accounting clicked a link.
Test the Kill Chain, Not Individual Controls
Most pentests evaluate controls in isolation. But real attacks chain multiple weaknesses together. The attackers who hit M&S didn't just make a phone call—they used that access to harvest credentials, move laterally, exfiltrate Active Directory data, and deploy ransomware across VMware hosts.
A valuable pentest simulates complete attack scenarios from initial access through data exfiltration. You might discover your endpoint detection catches the malware, but your SOC doesn't notice the alert for 72 hours. That's actionable intelligence worth far more than a list of CVEs.
Address the Shadow AI Gap
With 63% of organizations lacking AI governance policies and shadow AI adding $670,000 to breach costs, this is low-hanging fruit for competitive differentiation. Before your next enterprise security review asks about it, get ahead of the question.
ISO 42001 certification demonstrates AI governance maturity. Most consultants don't offer it yet. Companies that achieve it first will have a significant advantage in enterprise sales cycles where AI risk is increasingly top of mind.
Demand Deliverables That Drive Action
Your pentest report should do more than document findings. It should accelerate remediation and enable business outcomes:
- Executive summary your board can understand in five minutes—with business risk, not just technical jargon
- Prioritized remediation roadmap based on actual exploitability in your environment, not generic CVSS scores
- Attack narratives that show exactly how findings chain together—perfect for security questionnaire responses
- Specific remediation steps your team can implement, not vague recommendations like "improve access controls"
- Retest validation confirming fixes actually work—documentation you can share with prospects and auditors
The Bottom Line
A penetration test is an investment. Like any investment, the return depends on how strategically you deploy it.
Used poorly, it's a $15,000 to $50,000 checkbox that provides false assurance. Used strategically, it's competitive intelligence that hardens your defenses, accelerates enterprise sales cycles, satisfies increasingly demanding security questionnaires, and positions you as a trustworthy partner in an era of supply chain attacks.
The difference isn't the test itself. It's the thinking that goes into it.
Your next enterprise deal is going to ask about your security posture. Your next board meeting will want to know about ransomware readiness. Your next compliance audit will dig deeper than the checkbox.
Stop testing for compliance. Start testing for survival. Because in 2025, that's what separates the companies that close the deal from the ones that become the headline.
Ready to Make Your Next Pentest Count?
At Careful Security, we don't just run penetration tests—we implement complete security programs. Our 90-day audit readiness guarantee means you get certified faster, with findings that actually get fixed. Because the goal isn't a PDF. It's protection.
Schedule a consultation: carefulsecurity.com/get-started
Sources:
1. IBM Cost of a Data Breach Report 2025
2. Verizon 2025 Data Breach Investigations Report
3. MITRE ATT&CK Framework
4. CSIS Significant Cyber Incidents Timeline 2025


